Navigate towards your security objectives with a structured, field-tested action plan
Our Maturity Activity Roadmap begins with a comprehensive assessment of your security program, examining critical factors across governance, people, processes, and technology. The resulting plan includes estimated costs and resource requirements, providing a clear path to achieve your security objectives. The hole Secure development lifecycle is taken into account.
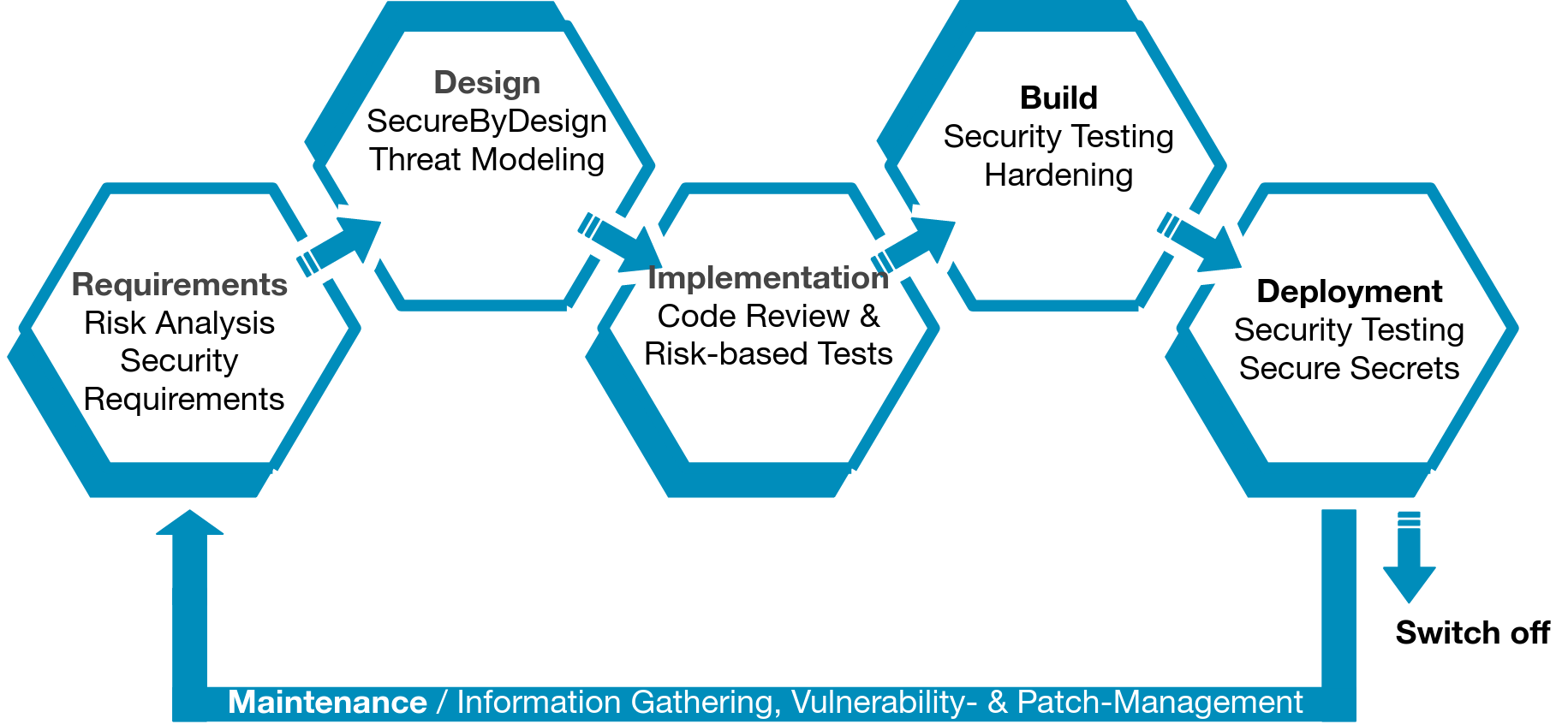
Understanding your used processes and tools is important in order to prioritize activities in your application security program.
We utilize the potential of OWASP DSOMM as a base
Our DevSecOps maturity program template uses dimensions understandable by developers and operations, for example:
Create your cloud security maturity program! Our model takes key dimensions into account:
We guide you in crafting a tailored security testing strategy, leveraging a powerful combination of SAST, DAST, SCA, and IAST. Our expertise extends beyond tool selection to help you effectively manage and prioritize discovered vulnerabilities, ensuring a robust defense against emerging threats.
Transform potential risks into opportunities for strengthening your security posture. Let us help you build a comprehensive, efficient, and compliant security testing framework.
Align your security testing strategy with EU regulations like DORA, which mandates robust vulnerability detection processes, by establishing continuous testing practices throughout the software development lifecycle.
Our approach incorporates cultural considerations. We employ diverse strategies to involve individuals in security practices. We assist in developing a reward system that evolves with your organization’s maturity, offering incentives such as:
Our methodology also includes establishing a security guild and fostering security-related communication.
We help you maximize the potential of each activity within your AppSec journey.
Continuously monitor the defined activities to detect misalignments and potential improvements.
Multiply security influence through Champions. Fortify their skills through specialized, context-aware security courses.
Implement security checkpoints at every phase of your CI/CD with our experts.
Design your architecture with security in Mind through early threat modeling. Uncover potential threats and implement safeguards before coding starts.
A comprehensive asset inventory drives AppSec Program success. It lists all your applications and might list all third party dependencies (e.g. Open Source).
Leverage our guidance on process definition and tool evaluation and optimization.