Navigate towards your security objectives with a structured, field-tested action plan
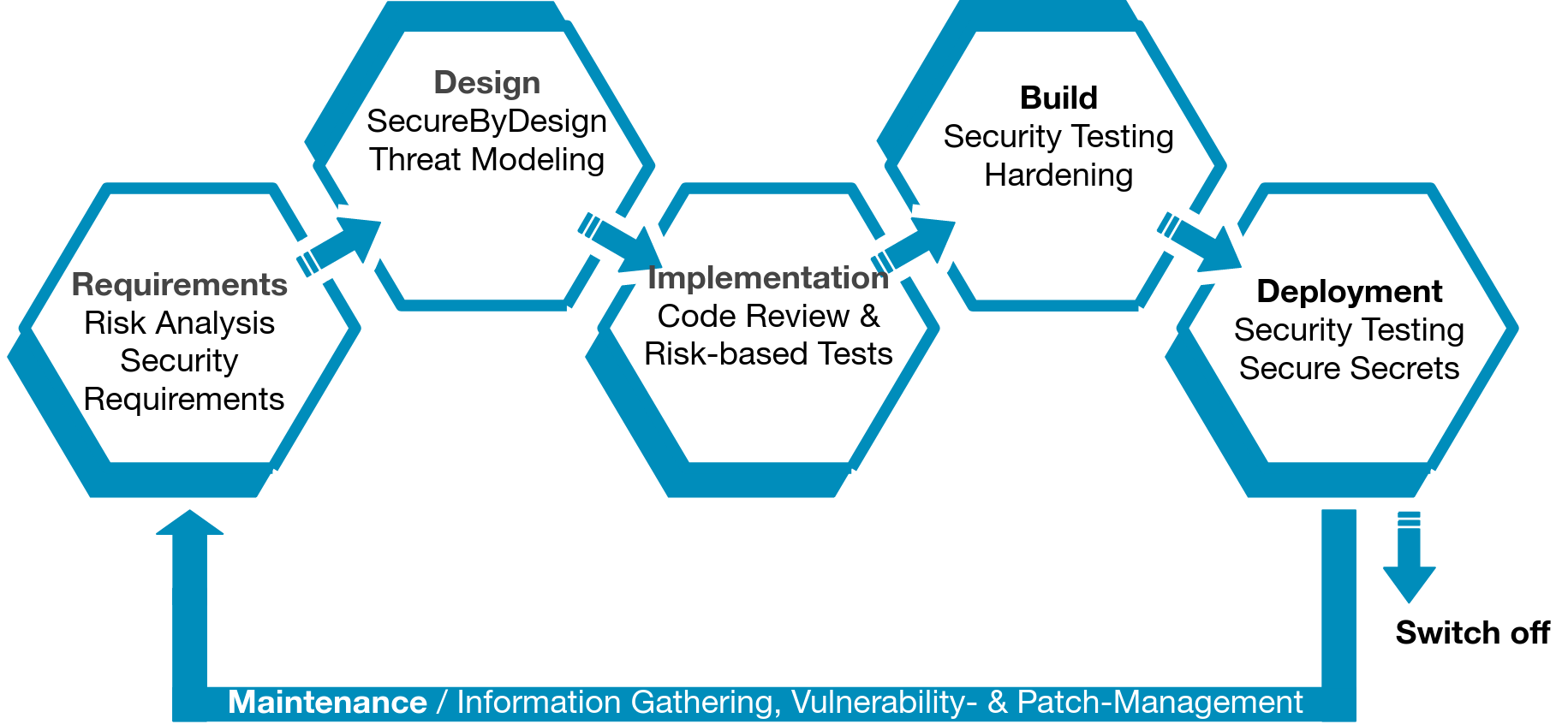
Our Maturity Activity Plan begins with a comprehensive assessment of your security program, examining critical factors across Governance, people, processes, and technology. This analysis Reveals your current security posture, Helps define your target state, Outlines a strategic roadmap. The resulting plan includes estimated costs and resource requirements, providing a clear path to achieve your security objectives. The hole Secure development lifecycle is taken into Account.

Reveal cross-functional challenges, like balancing audit requirements with innovation goals.

Prescribe automation processes to reduce the reliance on human intervention, enabling the elimination of bottlenecks and an increased focus on more meaningful challenges.

Measure your organization's capacity and ability to maximize capabilities relative to your unique risk profile.

Develop a holistic plan to optimize the speed of activities in relation to ROI of associated capabilities.

Discover the opportunity cost associated with your decisions, such as balancing quick wins vs. scalable solutions.

Determine the optimal testing process by looking at the mean time it takes to identify root cause across varying analysis and testing methods.

Increase confidentiality, integrity, and availability by understanding the impact of each security capability and its associated risk to achieving program goals.
Understanding the health of your applications starts with an look at your security tools, projects, and people. By capturing a holistic view of your security posture, you can build a plan to thoughtfully address security gaps.
A Software Security Program MAP helps you:
Are you looking to move your applications to the cloud but aren’t sure how to maintain security as you do it?
A Cloud Security MAP provides you with a clear security strategy for managing your cloud-native applications. Each Cloud Security MAP is developed using proven Synopsys cloud security maturity models along with industry-recognized frameworks (CIS, NIST, etc.).
A Cloud Security MAP helps you:
Developer productivity and pipeline velocity doesn’t have to come at the cost of security. Implementing a Synopsys DevSecOps MAP can help you methodically integrate security into your pipelines without interfering with the speed of development.
A DevSecOps MAP uses a phased approach to help you:
Automate tools into your CI/CD pipelines
Draw up a plan to transfer best coding practices over to your developers
Identify and remediate vulnerabilities faster while avoiding development friction
Can you trust the open source that your developers are using? The Open Source Software (OSS) MAP provides you with a tactical roadmap to securely consume and distribute open source software while maintaining license compliance and avoiding risk for your applications.
The OSS MAP framework aligns with OpenChain, the international standard for open source license compliance.
The OSS MAP helps you:
Understand your license obligations
Utilize software composition analysis to find vulnerabilities and defects early in the SDLC and fix them
Put the proper governance and policies in place to manage the legal, security, and operational impact of OSS
If your organization has other software security needs, our customized MAPs can help you achieve them in the most cost-effective, efficient manner.
Explore how to train and nurture security champions within the software development team, to introduce, mature, or improve a security program.
Determine what’s working, what isn’t, and what you need to change, with a security metric–driven approach.
Learn how to integrate security into all stages of your existing CI/CD pipeline.
Early in the design phase—before code even gets written—discover how and where to implement secure design practices.
Manage security from a holistic point of view by understanding the depth and breadth of your full application portfolio.